Table of contents
Threat Catalog Copy link to clipboard
A Threat Catalog contains Threat Classes which can be used across multiple TARAs. I eases updating Feasibility Ratings throughout the entire TARA lifecycle. Threat Scenarios may refer to Threat Classes in order to derive the cause of compromise. But most importantly, Attack Steps refer to Threat Classes and derive the Threat Classes' Feasibility Rating.
itemis SECURE contains a predefined default Threat Catalog to help in kick-starting the threat modeling activities. This model contains the basic STRIDE Threat Classes and additional, customized sub-classes for a more detailed analysis. You may adapt the catalog contents to your needs.

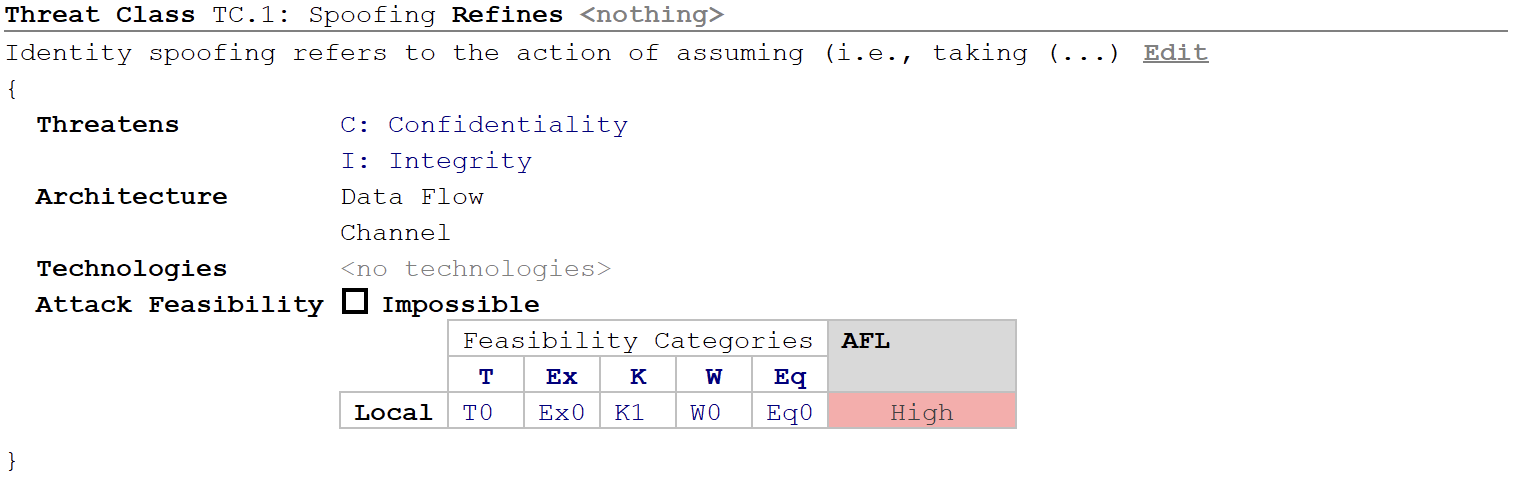
Threat Classes can be defined or modified in the main editor window. A Threat Class contains the following properties:
- Description General description for the item.
- Threatens Cybersecurity properties threatened by the Threat Class. (Multiple cybersecurity property selection is possible.) Further customization of the cybersecurity properties possible in the Method Configuration.
- Architecture Define the system element type (e.g. data flow or component) on which the threat is acting on.
- Technologies Technologies can be linked to the threat to help the analysis. Technologies can be also customized and extended, see more information in chapter Technologies .
-
Attack Feasibility: Attack Feasibility definitions can be customized per Feasibility Category and the
AFL(Attack Feasibility Level) is calculated automatically. The feasibility model can be customized in the related method configuration. Details can be found in chapter Method Configuration .- ET: Elapsed time
- SE: Specialist expertise
- KoIC: Knowledge of the item or component
- WoO: Window of opportunity
- Eq: Equipment needed
STRIDE Copy link to clipboard
STRIDE is a model for identifying and categorizing cybersecurity related threats. Each defined threat category corresponds to one cybersecurity property. The cybersecurity properties are the basic CIA (Confidentiality, Integrity, Availability) and additional extended properties as Authenticity, Authorization and Non-repudiability.
|^.
| Threat | Cybersecurity property | Threat manifestation |
|---|---|---|
| -. | ||
| Spoofing | Authentication | Pretending to be another entity |
| -. | ||
| Tampering | Integrity | Unwanted modification of data |
| -. | ||
| Repudiation | Non-repudiation | Claiming that an action is done by another entity |
| -. | ||
| Information Disclosure | Confidentiality | Providing information to an entity normally not entitled to access |
| -. | ||
| Denial of Service | Availability | Preventing the normal provision of service |
| -. | ||
| Elevation of privileges | Authorization | Allowing an entity perform actions normally not entitled to |
ASRG Threat Catalog Copy link to clipboard
The ASRG community Threat Catalog can be used for the whole life-cycle of a vehicle for:
- Creating new TARAs, to start with a set of actual threats
- Actualize already existing TARAs with the latest updates to maintain risk levels
- Incorporate a new class of attacks
A continuously maintained threat catalog can be beneficial for suppliers and service providers to extend their catalogs, but can be used by OEMs to tailor their own catalogs. Import and export is also possible via openXSAM format.
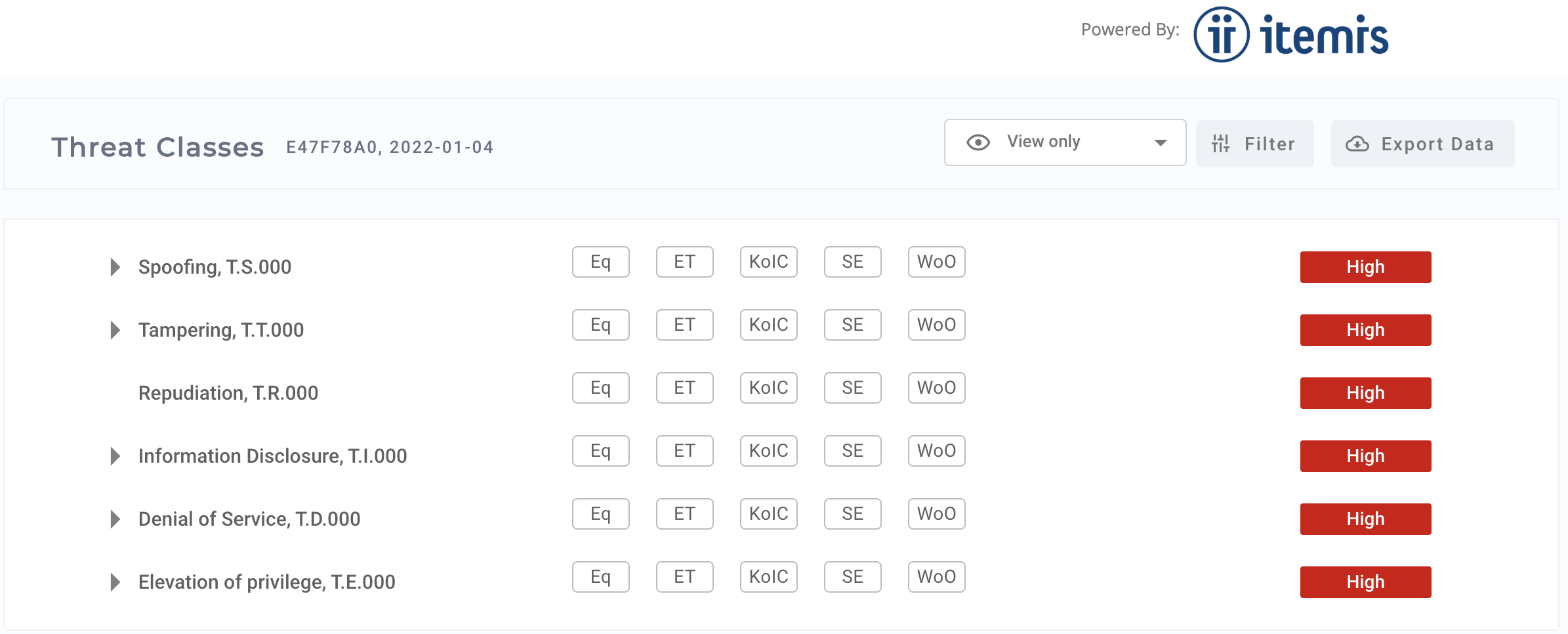
Threat catalog can be downloaded and imported into itemis SECURE. Further information on ASRG Threat Catalog can be found at https://garage.asrg.io/threat-catalog//.