Table of contents
Threat Scenario Identification Copy link to clipboard
Goal: Identification of Threat Scenarios as a starting point for the Attack Path Analysis
On our way to the first Risk Level, which is based on potential impact on the one hand and an Attack Feasibility on the other hand, we need to cover Threat Scenarios next. A Threat Scenario is a potential, rather high-level attack. It is realizing one or many Damage Scenarios and is itself realized by a set of attack steps (oftentimes also called Attack Tree). As with Damage Scenarios, it is possible to create the Threat Scenario elements manually in the respective chunks. The following image depicts the editor, followed by a description of the properties. It is recommended to use the Threat Scenario Identification Assistant to get to an initial set of Threat Scenarios in a structured manner.
Threat Scenarios can be edited using the editor depicted below:
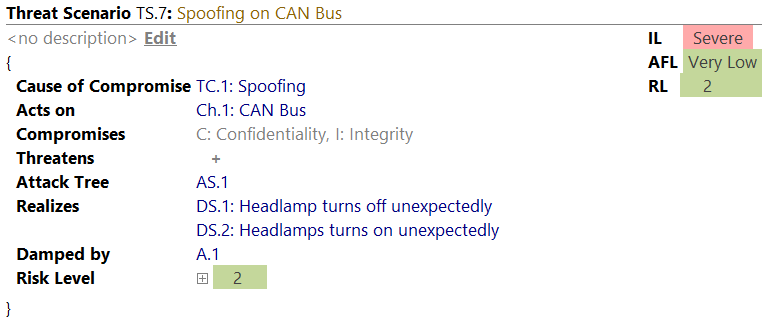
A Threat Scenario consists of the following properties:
- Name: Short identifier of the Threat Scenario, e.g. TS.1
- Title: Descriptive title of the Threat Scenario, e.g. Spoofing on CAN Bus
- Description: Description of the Threat Scenario
- Cause of Compromise: STRIDE-Category that is the cause of compromise. The selection is based on the active Threat Catalog which can be organized to the user’s needs.
- Acts on: Affected system element of the Threat Scenario
- Compromises: Read-only list of the compromised cybersecurity property. The information is derived from the cause of compromise (e.g. spoofing might lead to breaking confidentiality and integrity).
- Threatens: Optional list of other Threat Scenarios, that are threatened by this one.
- Attack Tree: Related Attack Tree which realizes this Threat Scenario. Could be a single Attack Step or a complex tree including logical expressions.
- Realizes: List of Damage Scenarios that are realized by this Threat Scenario
- Damped by: List of assumptions that dampen the risk
- Risk Level: Calculated Risk Level. If expanded, you can see the Risk Level per stakeholder and Impact Category.
Threat Scenario Identification Assistant Copy link to clipboard
Instead of creating the Threat Scenarios in the corresponding chunk, you may also use the Threat Assistant. (Alternatively, if you followed the steps of the Trust Analysis as described in one of the previous sections, you can use the Interaction Assistant here instead of the mentioned Threat Scenario Assistant for a more structured process that takes prioritization of system elements with higher criticality ranges into account.) Using the assistant supports creating Attack Steps from the catalog-provided STRIDE categories. It will take care of linking the corresponding system element and Threat Class for you. The Threat Scenario Identification Assistant can be found in the Assistants folder.
The following image shows one particular example which is taking care of Threat Scenarios with regard to the CAN bus:

- Spoofing: This entry shows an accepted suggestion. The name of the created Threat Scenario is shown in brackets (e.g. TS.7). You can reset this suggestion which removes the corresponding Damages Scenario from your model.
- Tampering: In case you rejected a suggestion it will look as depicted here. The decision will be part of your model and a rationale can be given in the inspector window. This way it is clear that you did not forget about this case but ignored it intentionally for now.
- Repudiation: This entry has not been processed, yet. You may either accept this suggestion or reject it. Accepting it will create a Threat Scenario for you and link it with the system element and STRIDE category for you.